Digital Banking Fraud – The Context
The rapid shift of banking from conventional branches to digital payment channels is creating a revolution in digital banking fraud. What was before a small line of work has now turned into an international industry. Criminal groups now use complex technology to steal huge amounts. As a result, banks have to absorb huge liabilities to cover the losses their customers suffer due to fraud.
As digital payment channels have increased, so have the routes that criminals can use. And now that banks are moving towards Open Banking, the number of routes available are about to multiply. So the banks are likely to face a new set of challenges in terms of detecting and preventing fraud. After all, they are liable for the losses.
This post covers the main sources of banks’ vulnerabilities and explains the different ways in which frauds take place. It then examines how the vulnerabilities can be effectively addressed by adopting payment system best practices. The post also explains how a counter fraud management platform should lie at the heart of a bank’s digital services architecture. Such a platform should ensure effective, real-time oversight of the end-to-end digital payment transactions. An effective fraud management platform, analyzes the individual customer’s behavior as well as the context of every transaction. It then compares the results with the existing behavioral patterns to detect anomalies.
As criminals are using sophisticated technology, it is increasing banks’ exposure to complex types of frauds. Against this troubling background, banks should deploy a platform that uses cognitive computing and predictive modelling for real-time fraud prevention.
How & Where Frauds Happen
There are numerous routes for criminals to penetrate digital delivery channels and carry out thefts. In most cases it is the to poor security awareness among banking customers who can be easily tricked into giving their sensitive information. In addition, fraudsters carry out phishing scams, directing customers to dubious internet banking webpages to steal their data. Phone-based frauds are also widespread. Criminals pose as bank employees to persuade victims to give away their login details.
Criminals also use significant elements of social engineering for phishing type scams. They use information available on customers’ social profiles, post as government officials to take personal details and even intercept their mails to build an accurate customer profile, allowing them to impersonate them. The information gathered can be used to create a list of probable passwords to crack their online banking accounts. It can also be used to make fraudulent applications for financial products.
Infecting digital devices with malwares is also very common. Fraudsters use software which infect customers’ devices with malware that recognize when they are logging into online banking services. The software save their keystrokes, enabling fraudsters to steal their passwords. During an online banking session, both physical hijacking of the line and malware is used to initiate a financial transaction that a customer might mistakenly authenticate.
How are Banks Doing
For banks it is important to understand that digital payment channels attract a lot of attention from criminal groups. These channels process transactions worth billions of dollars every day. Now that the industry is facing criminal gangs using modern technology, banks can’t afford to use traditional manual methods of fraud monitoring and detection. These manual methods neither have the capacity nor the speed to meet the challenges facing banks today.
Traditional monitoring methods are the reason why high-profile data breaches have been making regular headlines. Yet only 37% of banks have completed or are undergoing transformation of their fraud management operations. In addition, only 16% of banks can detect fraud as it is attempted. For most banks it takes weeks to discover a new pattern in fraud.
Banks are investing heavily in alternate delivery channels to provide the real-time digital services that their customers want. However, they are failing to allocate sufficient resources to keep their services secure. Without implementing payment system best practices and having a real-time fraud prevention platform, many banks struggle to detect dubious transactions in real-time.
For smaller banks where resources are more constrained, large liabilities due to fraud can become a huge problem. Therefore, alternative approach to detecting and preventing digital banking fraud must be implemented.
Payment System Best Practices
So far it has been established that a technology-based strategy is the only practical response if banks are to succeed in protecting their brand reputation and customer trust. Considering the industry wide best practices, we recommend the following logical, physical and operational security measures:
1. Logical Security Measures
A. Dynamic CVV to Counter Shimming
Shimming refers to an attack that captures data by tapping directly into an EMV chip. A small, flat device containing a microprocessor and a flash memory card inserted inside a card reader. The circuit is energized through engagement with the chip while it’s in the card reader and the device sniffs the data. Although shimmers cannot use the data to fabricate a chip-based card, they can use it to clone a magnetic stripe card. While the data that is typically stored on the card’s magnetic stripe, it is replicated inside the chip on chip-enabled cards.
The chip contains additional security components not found on a magnetic stripe. One of those components is an integrated circuit card verification value or “iCVV”or “dCVV” for short (also known as a “Dynamic CVV”) generated at the time of transaction. The iCVV differs from the card verification value (CVV) stored on the physical magnetic stripe, and protects against the copying of magnetic-stripe data from the chip and using that data to create counterfeit magnetic stripe cards. The one of ways for an attack to be successful is if a bank card issuer neglects checking the iCVV & POS Entry conditions sent with each transaction. These conditions provide the issuer with necessary information on how the merchant or the ATM acquired transaction data when authorizing the transaction.
B. Asymmetric Cryptography
Acquiring banks should opt for encrypting “Point to Point” communication channels with additional RSA based asymmetric cryptography using Transport Layer Security (TLS 1.3 standards) along with secure hashing aka MAC-ing. This approach can prevent data leaks from replay & host ghosting attacks.
C. Remote Rotation of ATM Master Key
Remote rotation of ATM Master Key responsible for encrypting PIN, helps banks ensure that if symmetric keys are compromised, they become useless as master keys are regularly substituted. This also helps in replacing the dual operator or split knowledge implementation of keys on each ATM since it securely automates the whole procedure without any human intervention.
D. Two-Factor Biometric Authentication
Along with EMV based transaction processing, two-factor biometric verification can help secure the transactions. In two-factor authentication, ATM processor/controller invokes dynamic and randomized 1-10 fingerprint authentication flows.
E. Tokenization
Tokenization replaces the primary account number with a unique value or numeric sequence. It renders transaction data useless to criminals as they are unable to reverse the process to access the original data. This is why tokenization can play a crucial role when it comes to digital payment security. It helps protect sensitive customer information and prevent the losses caused by data breaches.
Many financial institutions are now using tokenization as a key part of their fraud prevention strategy. With this approach, a unique token is generated which can be used by a customer to make purchases. This way customer’s card details or account number is not needed to be shared. This makes the payments simple and secure.
F. 3-D Secure Version 2.0
At the PCI European Community Meeting in Barcelona in October 17, PCI Security Standards Council released a new security standard. It is about supporting EMVCo’s EMV 3D Secure Protocol and Core Functions Specification that follows the release of 3D Secure version 2.0.
The verification process in the latest release is one of the major changes. In this process, static passwords will be replaced by tokens and biometric. This will result in a much better experience for e-commerce customers. The new protocol facilitates data exchange between the issuer, cardholder and merchant. As merchants use biometric instead of old-fashioned passwords, it reduces the risk of fraud and help cut down card abandonment rates.
2. Physical Security Measures
In order to counter physical threats, ATM acquirers should deploy anti-fraudulent systems as part of an overall layered approach to ATM security.
- With anti-skimming detection sensors banks can detect card reader intrusions and stereo skimming attacks.
- Anti-card trapping detection sensors should be used. With automated alarm broadcasting to ATM processor banks can make the ATM machine “Out of Service” instantly.
- ATM fascia and cabinet alarms should be integrated online with ATM controllers for transaction monitoring data centers and disabling ATM on real time basis.
- PIN pad shields/guards should be used to prevent PIN prying attempts via pinhole cameras.
- CCTV coverage must be used instead of only relying on ATM image capturing solutions which may become incapacitated in case of the “Ghost in the Machine” (Malware) scenario.
3. Operational Security Measures
A. Penetration Testing
Web application penetration testing uses non-disruptive techniques to identify weaknesses in your application code and database layers which could be exploited during an attack. In many real-life cases where records were stolen, the method of compromise was attributed to simple errors that gave rise to significant vulnerability. Penetration testing is one alternative detective control that can highlight areas of risk created when overburdened system administrators inadvertently create vulnerabilities. Penetration testing of both web applications and network is necessary at least once in a quarter using services of more than one vendor.
B. Audit Trail
An audit trail or audit log is a security-relevant chronological record, set of records, and/or destination and source of records that provide documentary evidence of the sequence of activities that have affected at any time a specific operation, procedure, or event. Financial institutions must configure all customer data handling applications to enable audit trail. Transaction and system logs must be routinely audited.
C. PCI-DSS Compliance
Banks must achieve PCI compliance in order to standardize their security infrastructure for digital payment transactions. PCI compliance is a regular process containing various steps to ensure that banks technological environment is compliant with security requirements.
PCI DSS specifies periodic validation. Banks and financial institutions must periodically perform the assessment recommended by the standards in order to maintain security.
Cognitive Computing Holds the Key
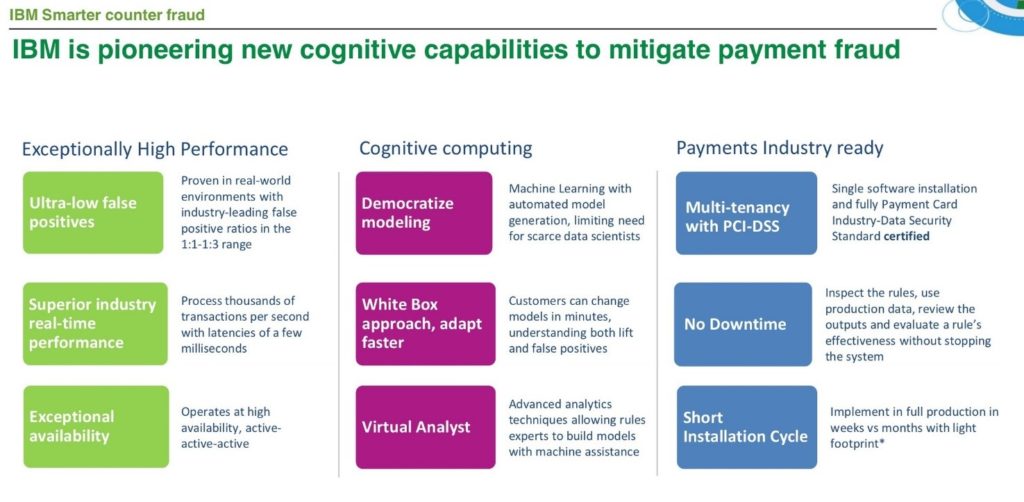
With payments cycles shortening, there is less and less time to counter threats. While machine learning techniques have long been used in the fraud world, applications have been constrained by the need for sophisticated data scientists and a dependency on “black box” models that are hard to understand, explain, and slow to adapt. A transparent “white box” and data driven approach is essential to control risk and costs.
As a certified IBM Partner in Financial Fraud Management, TPS is offering IBM Safer Payments – World’s # 1 fraud detection and management solution by Market & Market. The solution uses cognitive computing and predictive modeling to prevent fraud for all cashless payment channels including Credit or Debit Cards, ATMs, Digital Banking Platforms, Mobile Wallets, Payment Switches, Ecommerce Gateways, as well as ACH and Wire Transfers.
According to IBM’s 2015 Fraud in Financial Institutions Study only 56% of executives believe their organization is in reasonable control of fraud threats and a significant number believe their fraud operations organizations are in need of a substantial overhaul. The same study shows that only 16% of banks already have the capability to use the technologies needed to detect fraud before near-instantaneous transactions have actually moved money.
How Cognitive Computing Can Help
When it comes to preventing digital banking fraud, the trick is to detect it while it happens. A modern fraud program needs to be fast and accurate. It is dealing with short term and ever changing fraud patterns. It needs to be fast in detecting fraud, in finding patterns and in applying countermeasures. And if it can do this in real time, with an ability to do on-the-fly changes to the counter-fraud models, it’s even more powerful.
IBM Safer Payments bridges the gap between expert-driven rules and traditional predictive modeling by applying artificial intelligence to partner with human experts. It suggests ‘best fit’ analytics in an interactive fashion. The solutions acts as a “virtual analyst”. It identifies patterns and design models. The cognitive computing approach unleashes a new paradigm in fighting fraud. It provides dramatically lower false positives, radically faster scale and speed, and more control and transparency.
Countering Fraud in Different Channels
Fraud prevention is a common goal for all players of the payment ecosystem. However, what this exactly means is not the same for different types of payment companies. IBM Safer Payments provides each participant with a solution tailored to their specific needs.
1. Credit or Debit Cards
Card fraud prevention module offers specific and configurable reporting on merchant compliance, as well as a complete investigation workflow for merchants violating scheme rules or exposing high-risk behavior. It combines a very high fraud detection rate with ultra-low false positive rates.
For card-present purchases, POS acquirers usually do not bear the fraud losses. However, they must protect themselves against the default risk of merchants and ensure compliance with payment scheme rules.
2. ATMs
ATM acquirers have access to a massive number of non-financial messages exchanged on ATM network level, known as “machine events.” The module allows for merging such non-financial transactions to historical profiles and combines these with financial transactions. This enables the detection of ATM channel specific fraud, such as gas attacks, skimmer installation and cash trapping.
3. E-Commerce
Since E-commerce acquirers process card-not-present transactions, they bear the full liability of fraud. The fraud prevention module assesses the individual risk of each merchant and helps ensure implementation of payment scheme compliance. This enables each merchant to accept transactions based on their individual appetite for risk.
4. Online and Mobile Banking
The moment the payment fraud prevention solution identifies a high risk transaction, it is classified for further scrutiny and step-up authentication. This approach also provides compliance with various regulations, such as the revised Payment Services Directive (PSD2) issued by the European Union. The challenge is to provide not only fraud security, but also the best possible customer experience.
5. ACH and Wire Transfers
The module allows profiling payment behavior in multiple historical dimensions in real time. Artificial intelligence identifies emerging fraud patterns and automatically suggests new rules and scenarios to prevent fraud losses.
A significant number of users of this module are processors or switches that work for multiple banks or other payment providers. The module provides hierarchical multi-tenancy, including inheritance.
PA-DSS Certified
The payment fraud prevention solution is PA-DSS certified and designed to be hosted by a payment processor as a service to its processing clients. Each of its release is also PA-DSS certified. For financial institutions that process card data, this implies that when they undergo the certification, they only need to present IBM Safer Payments’ certificate to their QSA. Institutions that do not process card data can be reassured by the fact that IBM Safer Payments is certified to comply with the most comprehensive data security standard.
Solution Architecture
Banks can deploy IBM Safer Payments without overhauling their existing infrastructure. It can be connected with any internal or external channel including a transaction processing switch to detect frauds across all digital payment channels in real-time. The right approach is to deploy the solution at the heart of the digital payment infrastructure to ensure Omni-channel fraud detection.
Customer Success – Retail Banks
STET – French National Payment Switch
“With an average response time of less than five milliseconds per transaction even during peak periods when we are processing over 750 transactions per second, IBM Safer Payments enables us to detect potential fraud without adding any notable overhead to our service. In addition, we are able to respond to newly identified fraud patterns by deploying new countermeasures in a few hours without taking down the system.”
Pierre Juhen, Deputy CEO, STET
QIWI – Leading Alternative Payment Network in Eastern European
“IBM Safer Payments provides us with the confidence that we can immunize our services against any type of fraud patterns within a matter of hours.”
Anton Kuranda, Chief Security Officer, QIWI
COMDATA – Commercial Card Issuer in the US
“Our MasterCard portfolio had 12 basis points of fraud. With IBM Safer Payments we were able to reduce this to 2 basis points. At the same time we reduced our decline false positive rate to 1:3.”
Freddy Ramirez, Vice President – Risk & Compliance, Comdata
Closing Thoughts
According to a market research by Harris Interactive, 71% of customers will switch banks due to a fraud or a cyber-attack. Likewise, Edelman in its research estimated that 46% of customers will leave or even avoid companies with a security breach. Banking fraud therefore, is more than a boardroom issue.
As criminal gangs are coming up with complex methods using sophisticated tools, the traditional methods of securing payment systems are not enough. Technology is the only solution. Cognitive computing and predictive modelling techniques can bring superior insight and agility. As a result, banks can reduce false positives, lower losses to fraud, maintain brand reputation, improve customer service, enhance operational efficiency and save the time wasted on compliance.










One Comment
Very impressive