ABSTRACT:
Maintaining a SOC (Security Operations Center) is an important status symbol for various organizations. A very few SOCs are useful in counteracting/reducing cyberattacks and IT abuse, and there is no standard framework available and no clear vision on SOCs. Many organizations are still left for guidance on how to properly implement an SOC. This paper highlights how an SOC can be institutionalized, operated, and maintained. Our research is majorly focused on identifying and defining new approaches based on artificial intelligence and machine learning (behavior analyzer), future assessment on SOC, and how to draft a new design framework, to combat the cyberattacks and to assess and improve the effectiveness of the protection provided by an SOC
Keywords: Artificial Intelligence & Machine Learning (AI & ML); Behavior Analysis; Cyberattacks; Cybersecurity; Security Analytics; Security Operation Center (SOC).
I. INTRODUCTION:
a. What Is an SOC and Explain Its Mission?
A Security Operation Center (SOC) plays a vital role in integrated security intelligence technologies. It functions as a team with relevant knowledge and skills, operating based on well-defined processes, and it is supported by the network analysis system. The SOC focuses explicitly on protecting against cyber threats, monitoring networks, developing incident management systems, and preparing analysis reports.
Protect + Detect + Respond + Analysis Report = SOC Operations
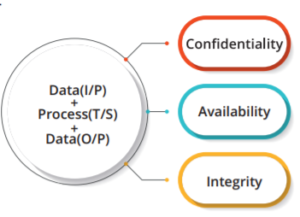
Under the umbrella of an overall cyber network security operations environment, we realize that user’s transactions and electronic data or information represent a particular value. This transaction of information/data between organizations and their relations can be roughly divided into privacy, sensitivity, and confidentiality (Shown in Fig1). The transaction of processed data is provided by information technology (IT) with its web application and data storage. From a security perspective, functionality and data are the principal objects to defend. One must ensure the confidentiality, integrity, and availability of IT service delivery.
Every organization that develops a piece of software needs to have a proper application security team to combat cyberattacks. Many organizations have adopted “secure service development” with sophisticated risk and vulnerability analysis methods, explicit security requirements involving an SOC team for penetrations tests and programming code reviews during development stages and verifying security acceptance criteria. The major part of an SOC operations team is to focus on the technical infrastructure, with the networks, external connections, office automation, mobile application solutions, and the servers running the applications and processing their data and information. The mission of the SOC team is to perform continuous monitoring vulnerability scans, compliance scans, log data collections, and so on.
Figure 1: Transaction of data
b. Knowledge and Skills for an SOC Analyst
There are many such firms (IT and non-IT) that are promoting preparedness (alertness) against cyberattacks by introducing various security measures. On the other hand, transformation of data from one end to other end over wired/wireless networks, logs, and alerts generated by security devices (IDS/IPS/Firewall, etc.) are increasing, adversely affecting many forms by these issues. It is crucial to determine if each log or alert is not a false positive, and the correctness of an event of a minor incident should be noted quickly and optimally. Therefore, a wide range of knowledge, skill and expertise is required:
• Network skills, security knowledge on cyberattack
techniques
• Vulnerability research skills
• Understanding of system and network environments
• Substantial knowledge of security devices
With such skills, there is an increased tendency for outsourcing the security monitoring and operation to run an SOC to an external specialist network security company, which is increasing. Following the trend, there has been a specific requirement for an SOC in any organization that sends threat intels to their customers; however, it is expected that the increase in complexity and advancement of cyberattacks, increases the demand for network security monitoring service/threat intels, which are provided by skilled SOC analysts.
II. LEVELS & ITS CURRENT STATUS – SOC OPERATIONS
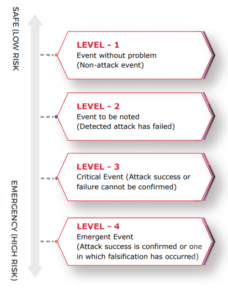
The SOC analyst performs a fundamental analysis on a massive volume of logs/records and alerts generated by network security devices to determine the importance and seriousness of each incident that occurs in the networks. In fact, the alert levels issued by network security devices (IDS/IPS) often differ from those concluded by the analysts, so the analysts determine whether or not an incident generated from logs is a false positive (wrongly indicates); if not, they will select the level of security events/incident as shown in Figure 2. Their analysis makes it possible to notify the users optimally (in the best) of only the significant events. The logs and alerts warnings sent from a single security device are generally insufficient to determine the level of the event. In such a scenario, the experience and knowledge of an SOC analyst on the system environment and the communication tendencies of customers will give better judgment as well as secondary data, enabling a FINAL decision (Shown in Fig 3) Such a situation highlights the difficulty of the analysis operations.
Figure 2: Level of SOC Operations
III. IMPORTANCE OF TOOLS AND TECHNOLOGIES IN SOC ANALYSIS (FACTORS)
a. Why an SOC Analyst Is Important?
An SOC analyst must focus on two factors:
1. Business knowledge
2. Infrastructure familiarity
The SOC analyst plays an important role in securing and enabling an organization. To do so, SOC analysts much have a fair prior knowledge and skills to understand the organization’s business and the values associated with the specific decision to focus on the most appropriate response. The SOC analysts need to have the technical infrastructure knowledge to maintain and manage incidents that support organization’s priority and to evaluate the real impact to organization. The SOC analyst also needs to share these technical bits of knowledge with the IT team of the organization. Moreover, the requirements from policies and standards can help support SOC operations to the organization’s overall risk and compliance posture by detecting and resolving high-risk behaviors and policy violations. The SOC analysts can produce security industry trends by comparing business-relevant information against available technical data, which can enable the business to improve decision making, risk management, and business continuity.
It is a saying that there are two types of organizations: those who have been hacked and those who don’t know they are. In this sense, a security breach is an event waiting to happen to any organization. When the attackers attack, it does not necessarily mean that the business will immediately experience a negative impact because attackers/hackers usually need time to accomplish their objectives beyond gaining unauthorized access to the network. Finding and protecting this type of behavior is just one of the many reasons organizations develop an SOC.
b. Certified SOC Analyst (CSA)
Every organization needs to create a framework for continuously monitoring system performance and improving its information security programs in the area of people, processes, and technology to combat cybercrimes. Therefore, every organization needs to have an SOC analyst or a certified SOC analyst (CSA) with better skills and knowledge to develop with the changing threat landscape and provide ongoing training to staff on cybersecurity best practices to adapt to deliver at a higher value. Finally, SOC analysts will always need to continuously improve their technical skills to assess their significance and effectiveness against evolving/developing internal and external threats.
c. Role of CSA
CSAs help an organization immensely to detect and analyze already-present internal cyber threats of the network quickly. Security analysis provides tools such as net forensic, network intelligence, and many more that perform the functions of specialist cybernetwork security services with graphical displays of rows and columns to make the job of a CSA specialist easier to spot trends and to detect suspicious activities that have been running over longer time frames. They also help to combat these suspicious activities.
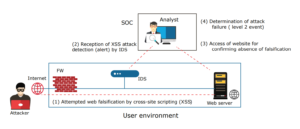
Figure 3: Investigation for cyberattack success or failure judgment
IV. SOC GENERATIONS
a. First Generation
In the first generation, logging messages were rarely visible by taking action to analyze and were instead referred to; if an event was reported, some sort of troubleshooting was required. The concept of information network security incident response was not adequately recognized because in this SOC generation, the process of identifying, communicating, and reacting to potential information security incidents was generally slow.
b. Second Generation
In the second generation, development of security information and event management (SIEM) tools was evidenced. The first generation of SIEM providers such as netForensics, Network Intelligence, and Cisco Security Monitoring, Analysis, and Response System (MARS) assured to detect network security threats. The SIEM providers of such tools focus on security threat management (STM) and security event management (SEM), which are used to deliver real-time log analysis for network threat detection.
These SIEM tools agree on log information generated by various sources in many formats, speeding up the process of detecting potential network security incidents or events. The purpose of SEM is to collect log information in the form of events/incidents from various sources of networking systems such as operating systems, security devices, and applications. Events are then correlated to identify the potential occurrence of incidents. The incident is then reported in the form of a dashboard alert to the operator to investigate further. The SEM function was eventually combined with the SIM function to produce what is known today as SIEM. The SIM tools focused on a search for a large amount of acquired log data. This historical data could then be analyzed for
different purposes. Another essential operational aspect introduced in the second generation was security incidents case management (SICM), in which SIEM operators can create and assign cases for security incidents reported by the SIEM tools.
c. Third Generation
In this generation, the SOC team would operate tasks related to vulnerability management; furthermore, the SOC team is involved in formalizing and executing tasks related to incident response. Vulnerability management refers to the procedures in which vulnerabilities are detected and confirmed, their impact is evaluated, corrective measures are identified and executed, and their status is tracked and reported until closure. Here, most of the time, sources such as MITRE, CVEs, and CWEs are referenced.
d. Fourth Generation
In this generation, the SOC concept is data improvement through the use of various sources such as domain name system (DNS) data, domain reputation service (DRS), Internet Protocol (IP), and geo data,. Network telemetry information is also being utilized for networks and security monitoring and turning; many commonly used network equipment are changed into security sensor ports. In addition, many new technologies are developed by the SOC for forensics and identifying network breaches, also known as breach-detection solutions. In the fourth generation, the SOC has expanded threat data sources, layering different security capabilities to battle more advanced threats, and automating cybersecurity to improve reaction time from hours to minutes in terms of incidents. This generation also provides policies to evaluate their abilities as a continuous process for optimization and improvement purposes.
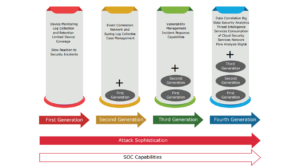
Figure 4: SOC – Four Generations
V. FUNDAMENTAL COMPONENT OF SOC
An essential component of continuous monitoring is the analysis of data collection carried out by the analysts working in the SOC. This is an enhanced activity since highly experienced analysts with acknowledged skills are in charge of both the preparation and management of complex network security investigations. A successful SOC analyst is an organization’s foundation for operational excellence and is driven by well-designed and executed processes, stable governance, capable individuals, and a constant drive for continuous improvement to stay ahead of cyber adversaries. SOC analysts need interdisciplinarity with highly specialized skill sets to combat current and advanced cybercrimes. However, the security community faces a serious shortage of such skills and qualified and certified candidates.
Moreover, many employees, because of lack of education and knowledge, leave the doors open to further cyberattacks. Since humans are the weakest link to security, average workforce happens to pick weak passwords, click on phishing links, and share company information on social media platforms.
A problematic factor for establishing cybersecurity is outsourcing. Many third-party vendors do not allow customer organizations to perform logging and monitoring. However, their engineers sometimes are leaving the door open for attacks as they do not necessarily keep a client’s security interest in mind. For such reasons, we introduced a new approach based on artificial intelligence (AI) to discover instant attacks, and to combat it, and future assessment on SOC to improve the effectiveness of the protection provided by the SOC analyst.
VI. SOC WITH ARTIFICIAL INTELLIGENCE AND MACHINE LEARNING
SOC with AI is aiming at saving workload in log analysis.
a. Proposed SOC Analyst and Reporting
In today’s cybersecurity world, SOC analysts have the difficult task of monitoring the massive volume of data to discover those pieces of relevant information that signify an incident worthy of action review. Presently many SOC analysts exploit signature, and rule-based tools are no longer useful in the current ecosystem. (The signature-based detection is used for detecting a more significant amount of false spontaneous messages, unauthorized commands between nodes, and buffer overflows.) Therefore, behavior-based analytics play a significant role in applying algorithms and statistical analysis to detect threats. SOC analysts can bring a unique value to monitoring activities. The SOC analyst can analyze data across various network systems and devices, providing visibility to individual development and patterns that may have been hidden otherwise.
b. Behavior-Based Analytics
Behavioral analytics is a recent advancement in the businesses that exposes a new insight into the behavior of consumers/users on eCommerce platforms, online games, web applications, mobile applications, IoT devices, and many more. Behavioral analytics employ behavioral analyzer tools, also known as kill chain Analyzers, which allow future actions and trends to be predicted based on the collection of such data.Behavior analytics is a category of different classes that analyze behavior for the indicator of compromise (IoC). Some of the groups are as follows:
1. Network-based behavior
2. Host-based behavior
3. User identity–based behavior
4. Cloud-based behavior
5. Dark web intelligence
Network-Based Behavior
These analytics are technologies that are on the lookout for lousy packet sniffing in the dataflow. Some other technologies available today that allow this capability are network behavior, sandboxing, and packet capture.
Host-Based Behavior
This analytics have a very busy area for challenging technologies. It is a system that monitors a network system on which it is installed to detect an intrusion; it responds by logging the activity and notifying the designated authority. A few technologies are sandboxing, system behavior, application whitelisting, statistical analysis, and memory monitoring.
Identity-Based Behavior
Identity-based behavior analytics provide with the capability of tracking user logins and actions across networks, applications, and spotting anomalies.
Cloud-Based Behavior
Cloud-based behavior analytics are a combination of AI and ML, big data, and analytics technologies to identify malicious, stealth behavior (secrecy) by analyzing subtle differences in normal, everyday activities in order to proactively stop cyberattacks before the attackers have the ability to execute their destructive plans fully. Cloud analysis is extremely difficult and is heavily dependent upon the cloud vendor.
Dark Web Intelligence
It is a security analytics technique that actively monitors “dark-web” for activities relevant to any specific business
house that include monitoring activities such as
• Phishing attacks
• Threats against the organization
This is frequently used for firm brand protection and personnel security.
VII. NEW APPROACH BASED ON AI – SOC
Network security monitoring services are developed to combat issues related to SOC analysis such as increases in the amount of log and record analysis work and the shortage of analysts. In this paper, we propose to set up a cyber threat analysis server with AI, the purpose of which is to save workload in log analysis.
Cyber Threat Analysis
It is a process in which the knowledge of internal and external information vulnerabilities relevant to a particular organization is matched against real-world cyberattacks. With respect to cybersecurity, this cybersecurity focused on combating cyberattacks represents a smooth transition from a state of sensitive security to a state of a proactive one. With the cyber threat analysis server, the feature vector of communication packets related to each incident, and the decision results of analysts are used as the learning data to build a learned AI. This is then verified with actual realtime data to improve decision accuracy (verification of data).
However, when the setting is changed to improve the accuracy of results to avoid false positives, the issue of avoiding false negatives worsens. Since it is essential to maintain false negatives as close as null, considering the properties of this service, the setting of the threshold values is tuned very carefully to avoid false negatives. Finally, the scope of AI can judge Level 1 and Level 2 incidents as well as false-positive decisions.
Even at the present stage, about 50% of the analysis logs compared to ex-status before using AI have been reduced successfully, thereby leading to improvements in the operational efficiency of the analysts. By using AI for auto analysis and the decision of minor events/incidents that occupy a huge part of the operations of analysts, they majorly focus on essential activities such as the investigation of methods for responding to the advancing attacks and improving their detection accuracy.
AI can promote standardization of the quality of monitoring services and encourage innovative efforts of the analysts. It will also help implement a high-quality service, equipped with a high detection capability of even advanced attacks. This new approach of AI technology plays an essential role in cybersecurity:
• Helps design countermeasure against unknown cyberattacks
• Helps propose security countermeasures
• Helps detect cyber threats
• Uses open-source intelligence to analyze cyber threats
• Uses the cyber-physical integrated analysis technology for criminal investigation support
VIII. FUTURE ASSESSMENT OF SOC
The future assessment of the SOC includes the ability to execute a facility of service to monitor multiple electronic devices logs, including servers and clients; and then the SOC must receive more logs and alerts than what are currently being provided.
To make this possible, it is necessary to make active use of AI to improve the function of filtering events/incidents of low importance and to prepare a process that allows analysts to analyze and make a decision only on essential incidents.
Some top-scale organizations have already introduced SOCs independently like private SOCs for integrated management of logs and alerts. On the other hand, considering the difficulty of employing SOC analysts in an organization, it is expected that cases of outsourcing vendors as the operations of private SOCs will increase in the future. SOC operation differs for various organizations. Besides, it is necessary to execute a function for filtering general incidents completely for private SOC, so that only the important incidents or events will be analyzed by the private service provider’s analysts.
The main aim of the SOC is to provide prompt, seamless (all-in-one) services, covering advanced incident responses, and to get accurate results. It includes investigation of system servers and clients in addition to the present simple incident responses, such as closure or shut down of a protecting devices like firewall port when an event with a high potential (incoming & outgoing) of an incident is detected, where it is necessary to provide better services to ensure protection against critical incidents.
a. SOC with Machine Learning
ML-based technology helps analyst in identifying the potential security advanced attacks from all the background radiation of daily incident traffic. As the desired result is achieved, highly skilled security team members, such as a certified SOC analyst (CSA program), can then be utilized for more specialized search and analytics-focused work.
Before ML began to be applied to network security platforms, inconsistencies were detected by watching network traffic for abnormal activity. Let us consider an example. When an advanced attack injects/penetrates in a network system, it starts creating holes in the network system activity as it tries to spread itself. And it’s a form of quantitative analysis because one could discover many holes with the number of dataflow interaction takes place from one user to another with an attack outbreak/occurrence. It is an obvious way to detect an abnormality because the numbers are big, and it is a different activity compared to normal. Many attacks are more fineness/detail than that. When you are trying to manipulate the details of an abnormal behavior, users need a much more finely polished approach to analysis. In this case, the user is required to bring statistical analysis methods to understand what’s normal in an environment; this is where the real field of ML begins to have a real effect.
Traditional cybersecurity controls are unlikely to detect the threat because high-privilege account (HPA) users operate with the necessary credentials, entitlements, and access permissions to perform their role. User behavior analytics (UBA) remove the invisibility clock that allows most HPA users to operate with a measure of privacy by detecting abnormalities behaviors associated with internal and external cyberattacks. UBA solutions can automatically flag abnormal account activity, and they are risk-ranked with context-rich intelligence that correlates user, system, network, system, and physical data with HR tips and clues. The SOC can also utilize analytics to understand metrics and performance measures. It can use some metrics/ parameters to facilitate operational advancement internally, while management can use others to make informed decisions when balancing the trade-offs (situation) between risk and cost. Thus, a thoughtful metrics and reporting framework can add value beyond security matters by also serving as a compelling communication vehicle for financial and operational concerns.
IX. EFFECTIVE FRAMEWORK OF SOC
Every InfoSec organization consists of a chief information security officer (CISO), reporting to the chief information officer (CIO), and they play a vital role within the mission and security goals of the organization. Moreover, every organization has a process for secure service development to make sure that only reliable solutions are handed over from the development phase to the production environment (See Figure 5). One of the major components of the SOC is “security by design function.” This is frequently combined with methods and processes for business impact analysis, risk analysis, and privacy impact assessment. Results from these analyses provide information about the requirements for confidentiality, integrity, and availability. The SOC activities are divided into the following five areas:
1. Intelligence function
2. Baseline security function
3. Monitoring function
4. Penetration testing function
5. Forensic function
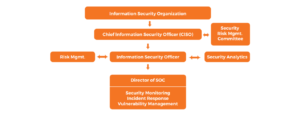
Figure – 5 Flow Diagram of Security Operations Center (SOC)
Intelligence Function
Intelligence function is with a computer emergency response team (CERT). Here, the knowledgeable, CSA-certified, experienced, and skilled analysts are located. This function plays a vital role in exchanging information with internal and external parties, analyzing threat patterns and monitoring results, defining rules for event filtering, and giving instructions to operational staff and network security staff.
Baseline Security Function
The SOC analysts for baseline security manage the operational processes for hardening servers, operating systems, and network components; they perform vulnerability and compliance scans to verify adherence to hardening guidelines. Moreover, they scan for known vulnerabilities and test the maintenance levels based on actual guidance on high priority and security patches. This function also supervises the settings and operational effectiveness of the endpoint protection (e.g., antivirus), firewalls, public key infrastructure (PKI), intrusion detection and protection system (IDS/IPS), and so on.
Monitoring Function
The SOC monitoring function observes the network data traffic and attempts to discover anomalies. The massive volumes of logging data and signals are stored and filtered using a dynamic set of rules to find a needle in a haystack. One of their significant challenges is to tailor/modify the SIEM in such a way that only the important alerts are identified.
Penetration Testing Function
Penetration tests are used both as an essential part of network security service development and operational environment within the network. A penetration test can determine how a network reacts to an attack, whether or not a system’s defenses can be breached, which protection was defeated, and what information can be obtained from the system.
Forensic Function
The SOCs’ analysts are knowledgeable and experts in finding details in the network traffic data and logging infrastructure data. When forensic investigations are performed by the law enforcement agencies and office of integrity, these analysts help in collecting electronic evidence and make sure that the chain of custody of such evidence is maintained and their integrity is maintained.
For each function, the objectives and activities can be defined and converted into requirements for competencies/ skills, experience, and amount of certified and qualified number of expert staff. Here, we apply rule of thumb based on observation in existing SOCs.
X. CONCLUSION
The key proposal is not to re-invent the wheel multiple times. It makes no sense to create tens of SOCs, as we know that there is only a very inadequate number of certified and skilled analysts available, and many SOCs fight for certified (CSA), skilled, experienced analysts along with implementing and tailoring new tools and technologies (AI and ML) in a meaningful way to combat the cybersecurity attacks. Such problems can be solved by increasing scale/ size and identifying and defining new approaches. In this research paper, we majorly focused on new tools and techniques of AI and ML, future assessment on SOC and effective framework on SOC, with different design functions to assess and improve the effectiveness of protection, and detection provided by an SOC analyst.
XI. REFERENCES
1. https://digitalguardian.com/blog/what-security-operations-center-soc
2. https://www.researchgate.net/publication/306938995_Security_Operations_Centers_for_Information_Security_Incident_Management
3. https://www.researchgate.net/publication/261164882_Classification_of_Security_Operation_Centers
4. https://www.mitre.org/sites/default/files/publications/pr-13-1028-mitre-10-strategies-cyber-ops-center.pdf
Authors:
Salman Khwaja
Manager Application Security, TPS Pakistan Pvt. Limited
Niamathulla SK
Product Manager – Content Research, EC-Council, India
Originally, published by EC Council.
Copyright © by EC Council. All Rights Reserved.










Leave A Comment